Daily Goal – AWS CloudFormation Challenge Labs
Challenge Lab – Provision and maintain AWS resources using CloudFormation
Scenario:
In this lab, I practiced provisioning and making changes to AWS resources by using AWS CloudFormation. First, I downloaded a CloudFormation template, and then I deployed a CloudFormation stack based on that template.
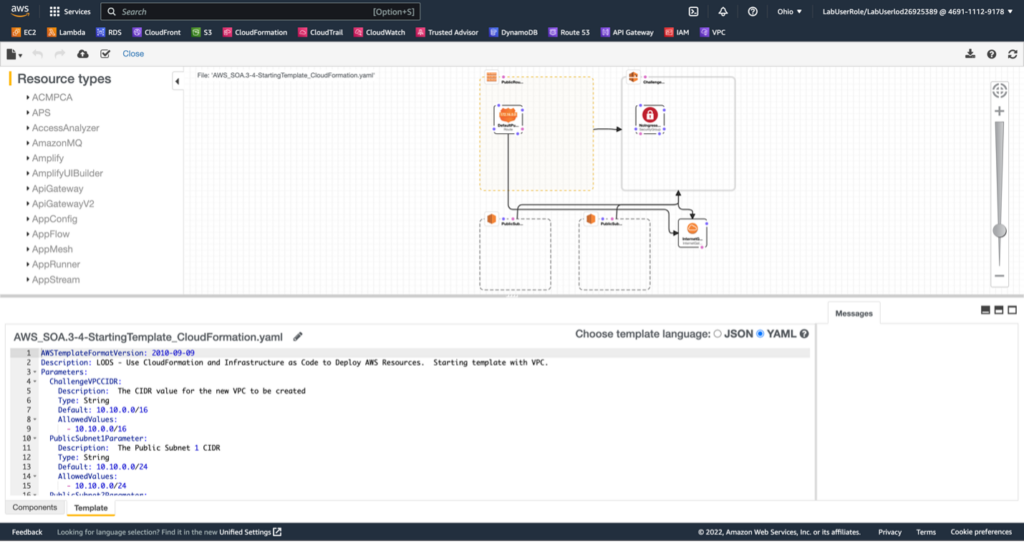
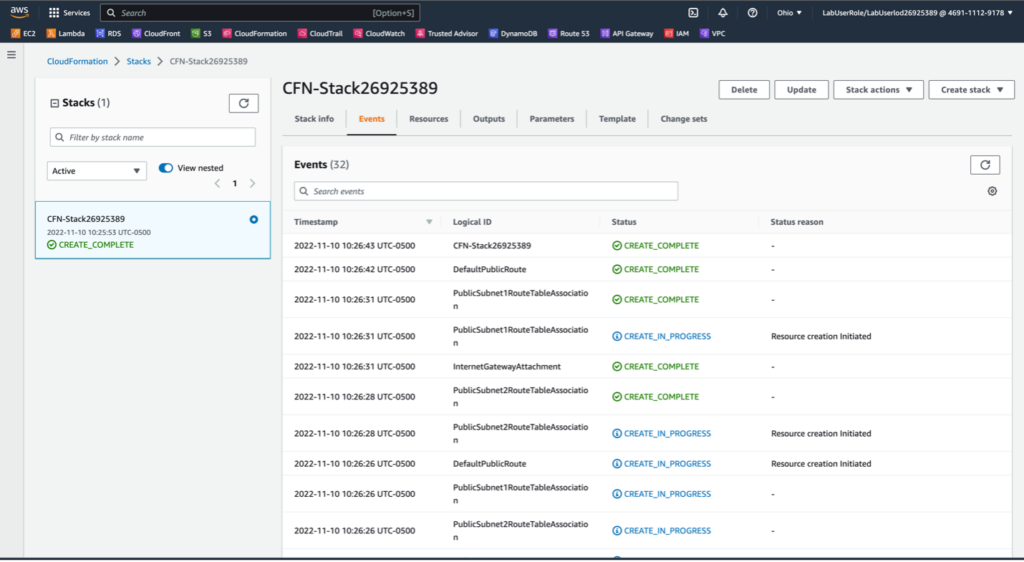
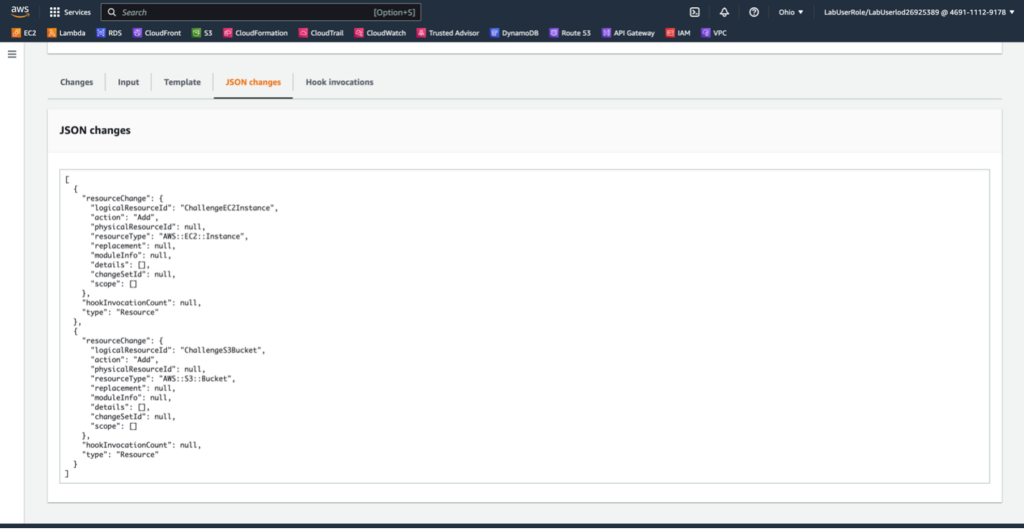
Next, I created a CloudFormation change set, and then I executed that change set to create an Amazon Simple Storage Service (Amazon S3) bucket and an Amazon Elastic Cloud Compute (Amazon EC2) instance.
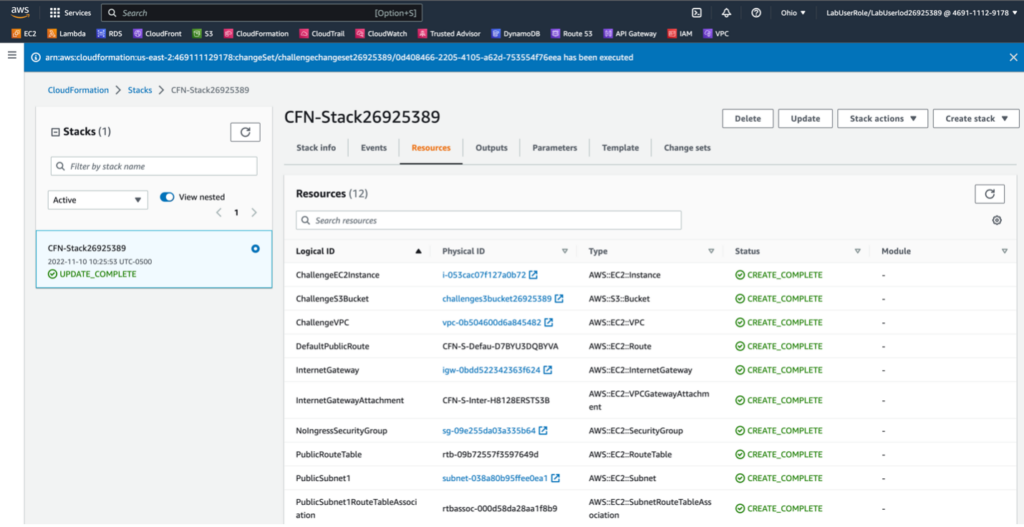
Then, I deleted the Security Group for the EC2 instance that was defined in the template and replaced it with the default Security Group for the default VPC.
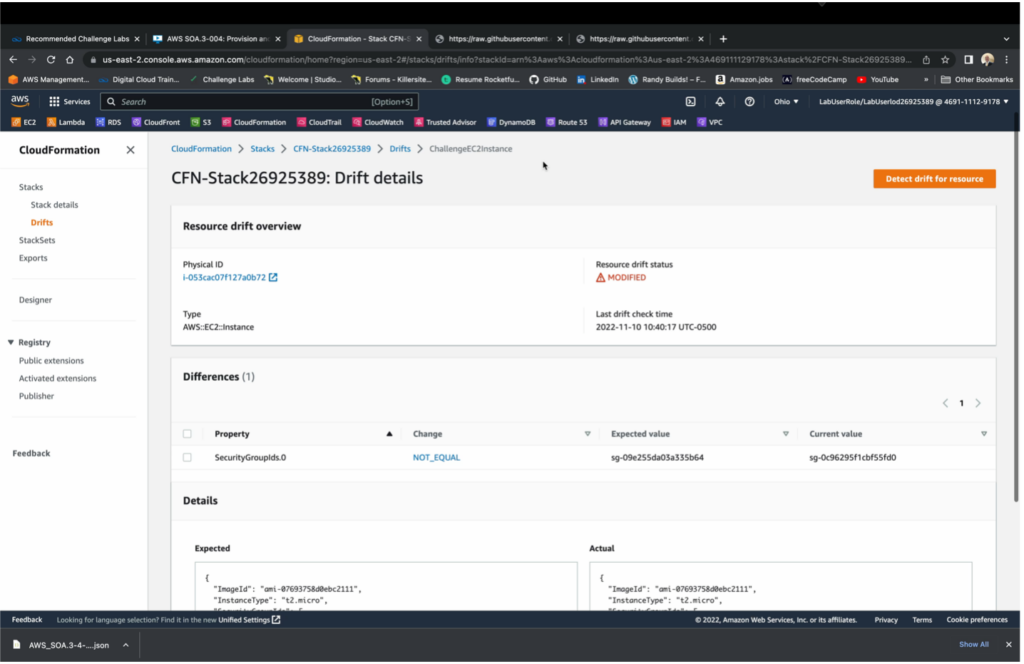
Finally, I detected those changes made to the EC2 instance by using CloudFormation drift detection, where I was able to easily compare the Expected SG stetting to the Actual SG setting. To conclude, I deleted the CloudFormation stack and all related resources.